Winlogbeat from the Beats Family of Elastic Stack can publish the Windows events either directly to Elasticsearch or Logstash. In case its configured for Logstash, the event logs sent by Winlogbeat can be considered as input to be further processed using the configured filters and generate the output to be stored in the Elasticsearch index. We can install Winlogbeat on multiple systems to push the event logs to a central system. We can further use Kibana to analyze and visualize the event logs. The whole process is shown in Fig 1.

Fig 1
This tutorial provides all the steps required to install Winlogbeat on Windows 10. It assumes that Java is already installed on the system and Elasticsearch, Logstash, and Kibana are already installed on the same system or accessible by the system. You may follow How To Install Java 13 On Windows, How To Install OpenJDK 13 On Windows and How To Install Java 11 On Windows to install Java. You can also follow the tutorial How To Install ELK Or Elastic Stack (Elasticsearch, Kibana, Logstash, and Winlogbeat) on Windows to get an overview of the Elastic Stack and to install Elasticsearch on Windows.
Download Winlogbeat
Open the Download Link to start downloading Winlogbeat. The download page provides options to download all the Beats as shown in Fig 2.

Fig 2
Click the Download Button to view the download options for Winlogbeat as shown in Fig 3.

Fig 3
Click the download link of the 64-bit version as highlighted in Fig 3. You may choose 32-bit based on your Windows installation.
Install Winlogbeat
In this step, we will install Winlogbeat from the Beats family on Windows using the zip downloaded by us in the first step. Extract the zip at your desired location and navigate to the installation directory as highlighted in Fig 4.

Fig 4
We need to edit the winlogbeat.yml configuration file as highlighted in Fig 4 to configure Winloagbeat. The default configuration of the Winlogbeat is shown below. It's pre-configured for event logs, Kibana, and Elasticsearch. By default, Winlogbeat is set to monitor application, security, and system logs as shown below. Also, note that it's disabled for Logstash and enabled for Elasticsearch by default, which means that it will directly send the logs to Elasticsearch.
...
...
winlogbeat.event_logs:
- name: Application
ignore_older: 72h
- name: System
- name: Security
processors:
- script:
lang: javascript
id: security
file: ${path.home}/module/security/config/winlogbeat-security.js
- name: Microsoft-Windows-Sysmon/Operational
processors:
- script:
lang: javascript
id: sysmon
file: ${path.home}/module/sysmon/config/winlogbeat-sysmon.js
...
...
setup.kibana:
...
...
output.elasticsearch:
# Array of hosts to connect to.
hosts: ["localhost:9200"]
....
....Now test the configuration before starting Winlogbeat using the command as shown below.
# Test Winlogbeat Configuration winlogbeat.exe test config -c winlogbeat.yml -e
It should pass the configuration test as shown in Fig 5.

Fig 5
This step assumes that the winlogbeat.yml is not modified since the default configuration will load the default index template after successfully connecting to Elasticsearch. Setup the Kibana Dashboards using the command as shown below. Make sure that Kibana is running before executing this command.
Fig 6
Now start Winlogbeat to start logging directly on Elasticsearch without Logstash as shown in Fig 7.

Fig 7
We can analyze the Winloagbeat Index, Index Pattern, and view the dashboard as shown in Fig 8, Fig 9, and Fig 10.

Fig 8

Fig 9

Fig 10
The dashboard will start showing the events as shown in Fig 11.

Fig 11
Similarly, we can run the Winloagbeat on multiple systems to collect the logs at a central location.
Winlogbeat With Logstash
In the previous step, we have started Winlogbeat using the default configuration to log the Windows events directly to Elasticsearch. In this step, we will configure Winlogbeat with Logstash. This step assumes that the Winlogbeat Index Pattern is created and Dashboards are already loaded on Elasticsearch. It was done in the previous step while running Winlogbeat for Elasticsearch.
Stop Winlogbeat by closing the window in case it's already running. Also, stop Logstash by pressing Ctrl + C if it's already running.
Update the Winlogbeat configuration by updating the winlogbeat.yml file to disable output to Elasticsearch and enable it for Logstash as shown below. Also, set the credentials in case Elasticsearch and Kibana are secured.
... ... #output.elasticsearch: # Array of hosts to connect to. # hosts: ["localhost:9200"]
...
...
output.logstash:
# The Logstash hosts
hosts: ["localhost:5044"]
...
...
Now again test the configuration before starting Logstash and Winlogbeat using the command as shown below. It must pass all the configuration changes done by us.
# Test Winlogbeat Configuration winlogbeat.exe test config -c winlogbeat.yml -e
We also need to configure the Logstash pipeline to accept the event logs from Winlogbeat. We can either update the pipelines.yml to specify the pipeline or simply provide the pipeline while starting Logstash as shown below.
# Logstash Pipeline for Beats
logstash.bat -e "input { beats { port => 5044 } } output { elasticsearch { hosts => [\"http://localhost:9200\"] index => \"%{[@metadata][beat]}-%{[@metadata][version]}\" } }"Now start Winlogbeat to push event logs to Logstash instead of Elasticsearch as we did in the previous step. We can further update the pipelines.yml file to apply filters to the event logs. We can further install Winlogbeat on multiple systems and push the event logs to the same Logstash.
An example filter to log events specific to the given event id is shown below. Logstash will drop all the events except for 8003.
filter {
if [type] == "wineventlog" and [event_id] != 8003 {
drop { }
}
}I have kept Elasticsearch, Kibana, Logstash, and Winlogbeat running for some time to collect enough event logs. The dashboard looks like the one in Fig 12.
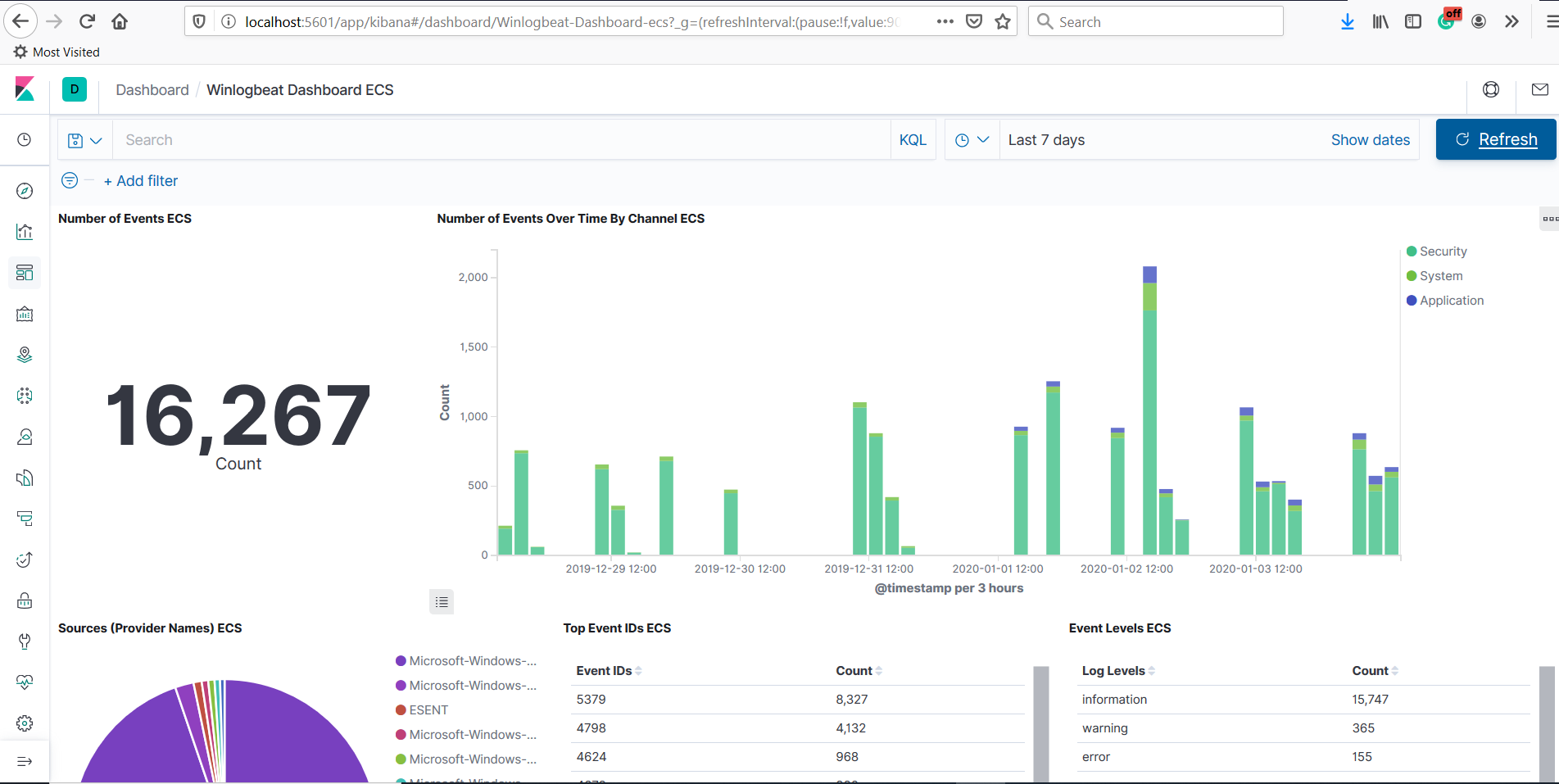
Fig 12
Install Winlogbeat as Windows Service Using PowerShell
In this step, we will install Winlogbeat as a Windows service using PowerShell so that it automatically starts on the system startup. It assumes that either Elasticsearch or Logstash configured with Winlogbeat is already running and active.
Install Winlogbeat - Extract the Winlogbeat zip file to C:\Program Files and rename the winlogbeat-<version> directory to Winlogbeat. We can even use the installation done in the previous steps. Configure Winlogbeat to either connect with Elasticsearch or Logstash to push Windows events.
Start PowerShell - Now search for PowerShell using the Cortana and run it as Administrator as shown in Fig 13. It will also ask for system permissions. Allow PowerShell to run as Administrator.

Fig 13
Navigate to your Winlogbeat installation and execute the command to install the service as shown in Fig 14.
# Install Service .\install-service-winlogbeat.ps1
# Uninstall Service
.\uninstall-service-winlogbeat.ps1

Fig 14
Now start the service using PowerShell using the command as shown below.
# Start Service Start-Service winlogbeat
# Stop Service Stop-Service winlogbeat
# Service Status
Get-Service winlogbeat
The Get-Service command will show the service status as Running after starting the service.
Summary
This tutorial provided all the steps required to install Winlogbeat on Windows 10. It also showed how to visualize the Windows event logs using Kibana by directly logging the events to Elasticsearch. The final step explained how to configure Winlogbeat for Logstash to log the events via Logstash.

